Introduction to DOS and DDOS
Friday 16 June 2017
Information Gathering (Overview, Tools and Techniques)
Posted by Unknown in: Ethical hacking tutorials
As we know from my previous post named five phases of ethical hacking, Information Gathering is
first and important phase of ethical hacking and penetration testing. The more
information you have about your target, the easy it will be to hack to your target.
What is Information Gathering ???
Information Gathering (also known as reconnaissance and footprinting)
is first phase of penetration testing and ethical hacking. It is process of
collecting relevant information(like ip address, hosts, nameservers, contact
info, employees, servers, antiviruses and intrusion detection systems etc.)
about target that helps in other phases of ethical hacking using various tools
and techniques like whois, netcraft, recon-ng etc.
Types of Information Gathering???
There are two main types of information gathering. Here is
short and sweet definition of both.
Active Gathering :- Active
refers to process of gathering information about target by directly interacting
with it.
Passive Information:-
In passive reconnaissance, we collect info about target without directly
interacting with it.
This post covers passive as well as active information gathering
concepts. Following is the list of some reconnaissance methods.
Google Hacking:- It
refers to collecting information from google using some commands called google
dorks. I have already written a post about using google commands. Have a look
at these posts.
Email Harvesting :-
It is technique of collecting all emails related to your targeted organisation
or website. There are various tools for gathering emails. But we will use theharvester tool in kali linux. Follow
these simple steps to gather email address:-
Step 1- Fire up Kali Linux and open terminal.
Step 2- Use below command to use theharvester.
theharvester –d cybrarytech.com –b google > mails.txt
-d - Used to specify target site. Here in
this example, I used it on my own site.
-b - Used to specify service which you want use
to collect emails. You can use google, bing, yahoo etc. I used google in this
example.
> mails.txt - This is used to store all the output in a
file. In this example, I stored all the emails in a file named mails.txt
Introduction to DOS and DDOS
Introduction to DOS and DDOS
Recon-ng
Recon-ng is very powerful framework for collecting target
information like hosts, contacts, profiles. You can think of it is a metasploit for
gathering information. But it is used for reconnaissance purpose only, not for
exploitation like metasploit. It is available in Kali Linux.
First of all, lets have a look at layout of its modules.
recon/domains-hosts/netcraft
recon – First part is name of module.
Domains-hosts – Second part is conversion action. This tells
that you have to give input as domain name of site and It will convert it to
hosts list relevant to that targeted site.
Netcraft - It is
third part, it refers to the source of gathering info.
Step 1 – To start recon-ng in Kali Linux, open terminal and
type recon-ng.
Step 2 – Now use below commands to use recong-ng
help - To get list of
commands.
show modules - To get list of available modules.
use - To use a module. For example.
use recon/domains-hosts/google_site_web
show options - Used to get options or particular module.
set -
Used to set option for
module.
run
- To run module.
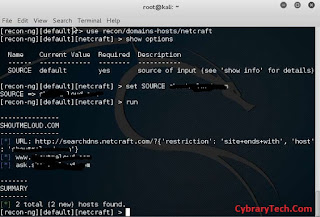
Finding available hosts of target site
For
the sake of tutorial, I will show you an example of how I got list of all
sub domains or hosts using recon. Have a look at below image in which I used recon/domains-hosts/netcraft
Using Additional Active Information Resources
Besides
these, we have some other resources to collect information about our target. Here is a small list of tools and techniques.
Netcraft.com
Using
this website you can get huge amount of information about your target like its
ip address, registrar, owner info, technologies or languages used in site. So
visit below link and enter ip address of your target site.
Whois
We can think of it as a database which can be used to
retrieve information like registrar, nameserver, registered date, expiry date
etc. Sometimes it reveals very confidential information about target. It is
managed by INTERNIC.
Whois tool is already installed in Kali Linux. Open terminal
and use below command.
whois google.com
You can use some websites for whois query too. List of some whois query site is below.
Using DNSEnum and DNSRecon to gather DNS Information
Both DNSRecon and DNSEnum can be used to gather DNS related
information like nameservers, mail servers, dns records(A,SOA,CNAME etc.).
These tools are free and available in Kali Linux.
Using DNSRecon:- DNS Recon can be used
for standard record enumeration, reverse ip lookup, server information
etc. For standard record enumeration,
open terminal in Kali and use this command.
dnsrecon –d google.com
Press enter and you will get many information nameserver,
mail server, A and TXT record etc.
Reverse IP Lookup is used to gather domain names associated
with any ip. Lets perform a reverse ip lookup using dnsrecon.
Using DNSEnum:- DNSEnum
is similar tool as dnsrecon. One thing I like about dnsenum is that, its output
is very understandable and formatted. Besides this, it is also very easy to use
this tool. Have a look.
Open Terminal and type this command.
dnsenum google.com
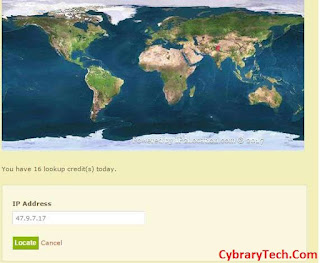
Geographical Location
Yup, it is also important to get geographical location of
target. Once, we have ip of the target, it is very easy to get its location.
You can ipaddressguide.com
for this. Open this site and enter ip address. Simple !!!
Hope you got enough knowledge about Information Gathering,
its types and Passive Information Gathering techniques and tools.
About Admin of the Blog:

Vijay Jangra is the founder of Cybrary Tech .He is a Tech Geek, Ethical Hacker, Programmer and a Pro Blogger. He is passionate about and love to learn new things about Ethical Hacking. Contact Him Here









0 comments:
Post a Comment